Administrator writeup
Administrator is a Windows Active Directory box that demonstrates permission chaining, BloodHound enumeration, and password‑spraying. We will use a recovered PasswordSafe database for credential spraying, perform targeted Kerberoasting, abuse DCSync, and finally use pass‑the‑hash to gain domain administrator access.
We are given a pair of credentials:
Olivia:ichliebedich
Scan the target with nmap:
They work on SMB.
Let’s use rusthound-ce collector to map Active Directory:
Load the collected data into BloodHound.
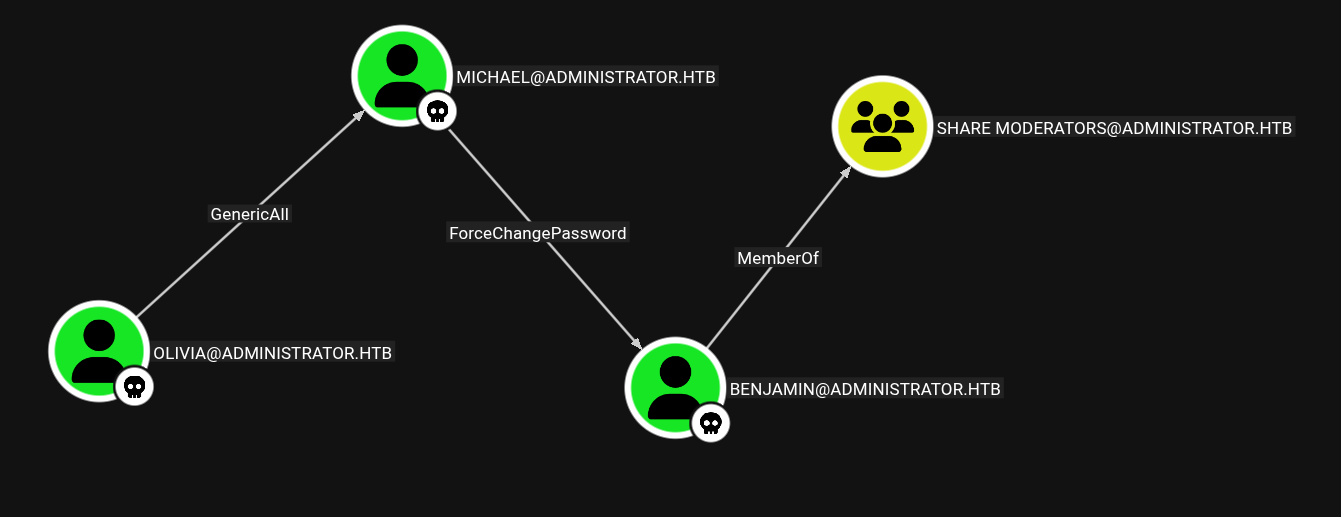
The owned user (Olivia) has GenericAll permission over Michael, which basically means we own Michael too.
And Michael has ForceChangePassword permission over Benjamin, meaning we can own Benjamin’s account by resetting his password, so we own Benjamin too.
And Benjamin is a part of the SHARE MODERATORS group, which would give you access to control shares.
Setting up a shadow credential is a better option than resetting the password, because if you do reset a password, it could prevent legitimate users from accessing Active Directory, and in a penetration test you want to ensure that there wouldn’t be a disruption of business operations as a result of your actions.
Though you can’t use that because there is no certificate service in this AD.
So you can use the net binary included with the samba package to change the password:
Or use autobloody to execute the full exploit chain from Olivia to Benjamin.
Now that we have valid credentials from a user in the SHARE MODERATORS group, let’s see what we can do with newly acquired FTP permissions.
Use binary mode, because ASCII mode can have awful encoding issues.
We have found a “password safe” file, which is a database for PasswordSafe password manager.
After we get in, copy their credentials to users.txt and passwords.txt files to perform a pitchfork‑type password spray.
And now we have valid credentials for Emily’s account.
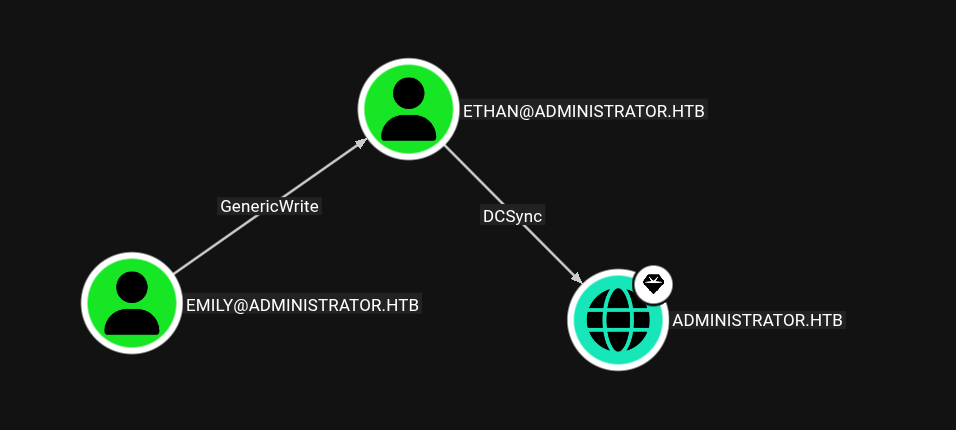
Looking at BloodHound again, our Emily’s account has GenericWrite over Ethan, and Ethan has DCSync over the domain admin.
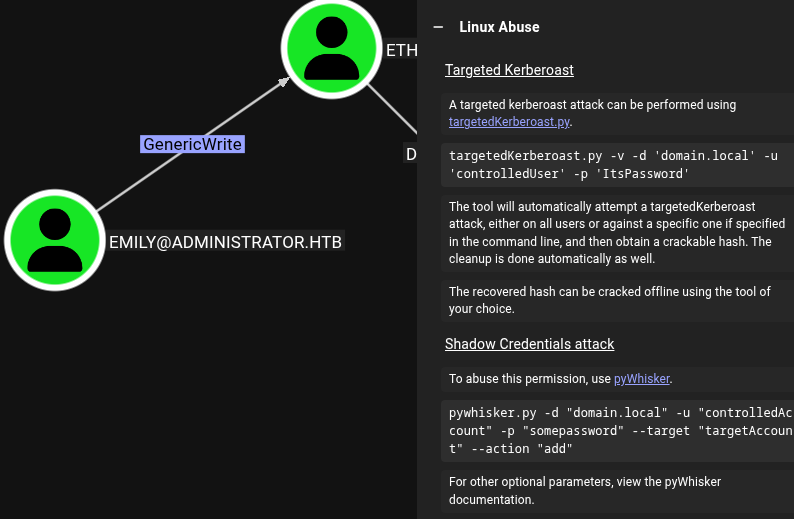
Using the instructions BloodHound gives us, install the targetedKerberoast.py script, then use it as described, but before that make sure to synchronize your clock to avoid the clock‑skew error.
Gets us ethan:limpbizkit credentials pair.
Then, because we have DCSync, let’s dump secrets by synchronizing password hashes with us:
Then use pass‑the‑hash to connect to the Administrator’s machine:
Credentials
Olivia:ichliebedich
Backup.psafe3:tekieromucho
emily:UXLCI5iETUsIBoFVTj8yQFKoHjXmb
ethan:limpbizkit
Administrator:3dc553ce4b9fd20bd016e098d2d2fd2e