Dog writeup
Dog is a Linux box featuring a Backdrop CMS web application. We will exploit source‑code disclosure via a publicly accessible .git directory, reuse MySQL credentials to gain user access, and escalate privileges through a custom bee binary that allows arbitrary command execution via its eval functionality.
Scan the target with nmap:
An nmap script finds a .git directory, which leaks the source code for the site.
Use git-dumper or an alternative tool to dump the contents:
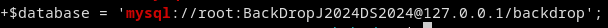
Find the first pair of credentials used to access the MySQL database:
root:BackDropJ2024DS2024
Use ffuf together with the aliases system to enumerate users without rate limiting from the login page:
Find out that the MySQL password works for the user tiffany.
You could use an exploit such as the following: https://www.exploit-db.com/exploits/52021
You might or might not need to repack it as a .tar archive for the upload functionality to work.
Check for password reuse to get a shell.
Check what commands this user can run with sudo:
bee appears to be a binary for managing the Backdrop application. Let’s see what it can do.
In the advanced tab of the help, eval looks promising.
Sending commands:
Or catching a root shell:
Credentials
root:BackDropJ2024DS2024
tiffany:BackDropJ2024DS2024