Fluffy writeup
Fluffy is a Windows Active Directory box that focuses on SMB share enumeration and NTLM hash capture. We will exploit CVE‑2025‑24071 via Responder, crack the obtained hash, then leverage shadow credentials and the ESC16 vulnerability to gain domain administrator access.
Check SMB access using the provided credentials.
Run a spider to enumerate share permissions and contents.
Connect with smbclient.py:
Find the CVE‑2025‑24071 exploit and locate a PoC on GitHub:
https://github.com/ThemeHackers/CVE-2025-24071/tree/main
Generate an exploit that points to your machine, so that when the target checks the file, it sends an authentication request to your address. This can then be hijacked using Responder.
Run a Responder instance waiting for connections:
Upload the exploit to a share where you have write permissions.
Crack the hash received from Responder using hashcat:
The password is recovered: prometheusx-303.
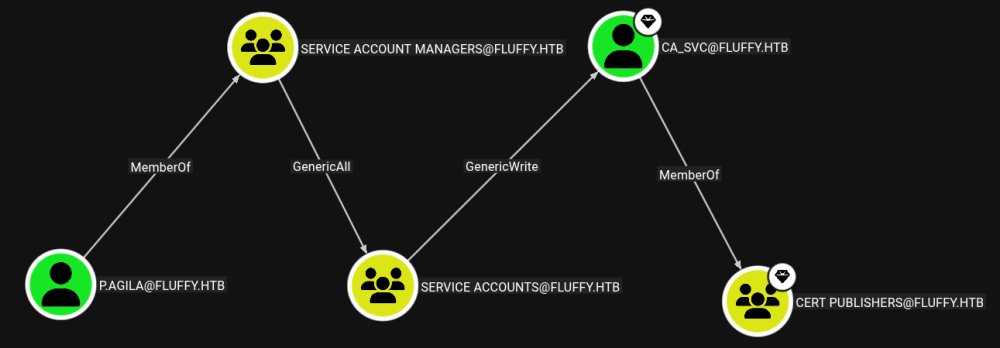
Add P.AGILA to the service accounts.
If you later face an “insufficient privileges” error while attempting the following steps, repeat this step (the lab periodically resets permissions).
Adding a shadow credential to winrm_svc (it’s on the same level as ca_svc). We can do this because we have GenericWrite permission.
After adding the shadow credential, we obtain winrm_svc credentials that can be used to get a shell.
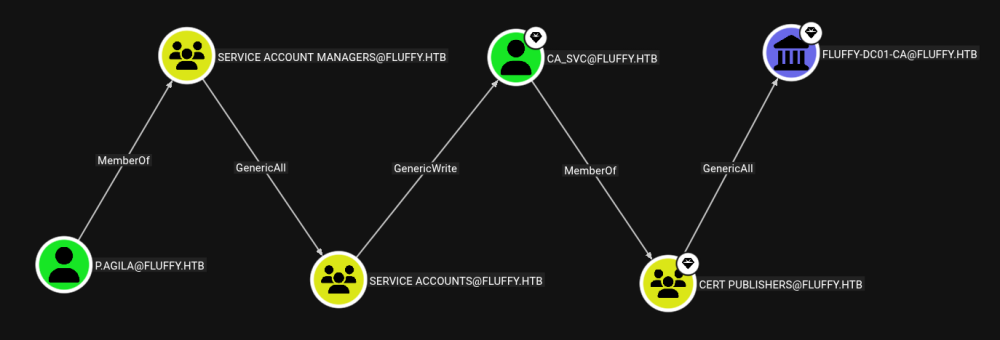
Now we can go the second route, going from SERVICE ACCOUNTS to CA_SVC instead of WINRM_SVC.
Check for vulnerabilities in the ca_svc account:
[!] Vulnerabilities
ESC16 : Security Extension is disabled.
Check the user principal name (UPN).
Change the UPN to administrator because we have GenericWrite permission, then use that to create a certificate with administrator privileges.
Before using the certificate, remove the administrator UPN from the ca_svc account to avoid a collision.
And we’re in!
Credentials
j.fleischman:J0elTHEM4n1990!
p.agila:prometheusx-303
winrm_svc:33bd09dcd697600edf6b3a7af4875767
ca_svc:ca0f4f9e9eb8a092addf53bb03fc98c8