How to use your own tools on remote machines via SSH socks tunnel
By using tunnels, you can forward only requests, without installing applications on the target machine
Also you get less latency, and you leave less footprint on the target.
Here are some examples to get started:
NMAP
ssh -D 9050 target@123.456.789.012
This will create a tunnel between you and the target, so any request you send to localhost:9050 will be forwarded through SSH to the target machine.
Then you can just use proxychains to wrap any tool, and it will use the port you specified in the config to forward requests.
proxychains4 nmap nmap -sn 192.168.0.0/24
You can do this with any tools that use outbound requests; nmap is just the best example.
Wireshark
Wireshark has support for capturing packets over SSH:
Go to Capture > Options
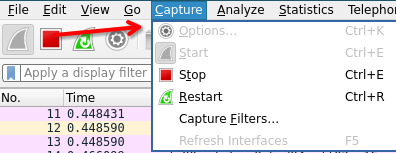
SSH remote capture options
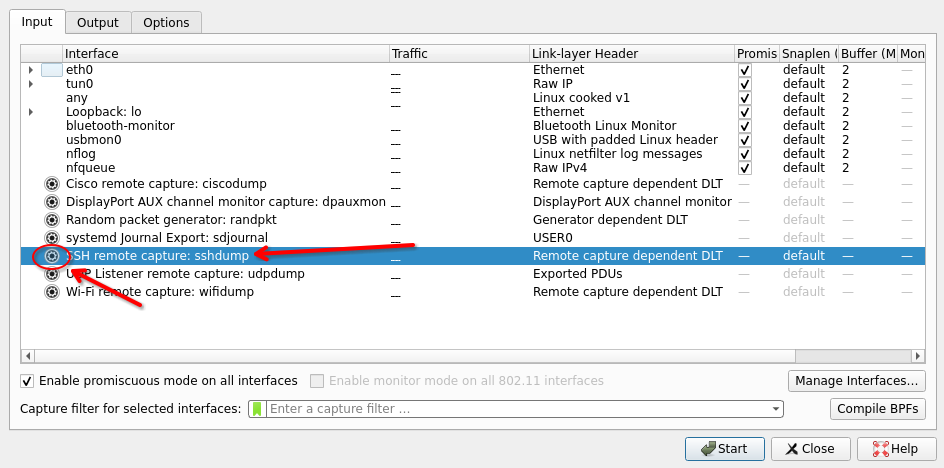
Configure authentication credentials, way of escalation to root, remote capture command, press start.