osu!gaming CTF 2025 web/admin-panel writeup
thanks to strellic for this challenge
263 solves / 109 points
Description:
we found the secret osu! admin panel!!
can you find a way to log in and read the flag?
expected difficulty: 1/5
Author: strellic
Download: web_admin-panel.tar.gz
The challenge consists of a two bug chain:
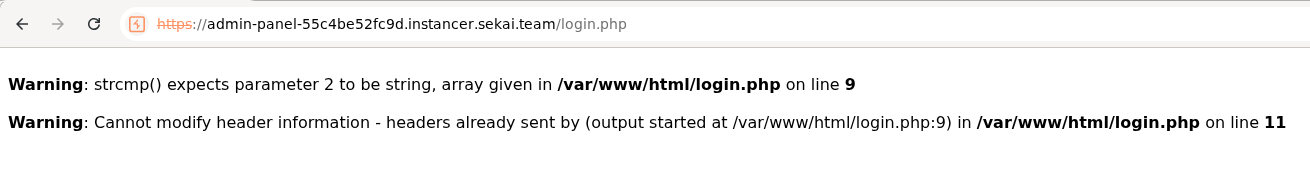
1) Auth bypass using strcmp() type juggling
The login code uses strcmp() to verify the password:
If you send an array instead of a string for the password parameter (password[]), strcmp() will return NULL instead of comparing strings.
PHP has two comparison operators:
==(loose comparison) - “kinda match” - compares values after type conversion===(strict comparison) - “exact match” - compares both value and type
The code uses ==, which performs loose comparison. When PHP compares NULL == 0:
- PHP converts both values to a common type
NULLgets converted to booleanfalse0also converts to booleanfalse- Therefore:
NULL == 0evaluates toTRUE
If the code used === instead, this exploit wouldn’t work:
So just send a request with username “peppy” (was hardcoded) and specify password using password[] to pass it as an array. The value of the password[] doesn’t matter.
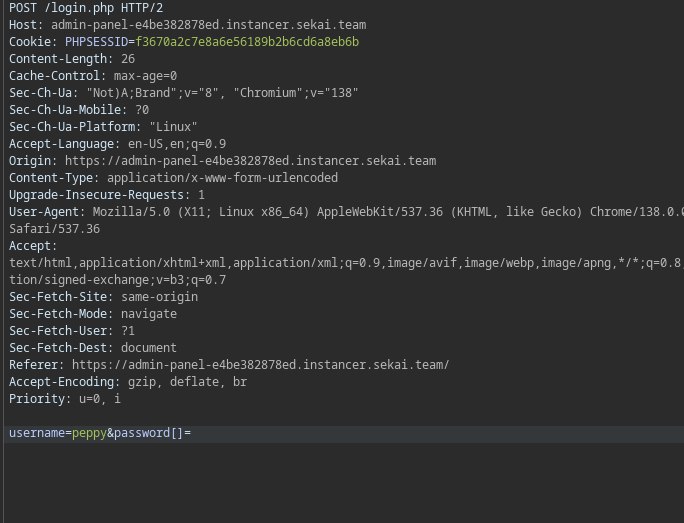
yes, it will result in an error, but it doesn’t matter because the state on the backend has changed so you can move to the admin.php page manually
2) PHP code execution using .htaccess override
The environment uses FROM php:7.2-apache docker image with default configuration that only executes .php files as code:
It means trying to avoid the first filter using other extensions like .phtml, .php5, etc. is meaningless because backend won’t even try to execute them. The only way to get code execution is to pass the .php extension through, but the filter wouldn’t let us. Or we can just bend the rules of what files can be executed as PHP code:
the default configuration contains:
.htaccess (Hypertext Access) is a configuration file used by Apache web server that allows directory-level configuration overrides. When AllowOverride All is enabled (as it is here), you can place a .htaccess file in any directory to modify Apache’s behavior for that specific directory and its subdirectories.
Normally, Apache is configured to only treat .php files as executable PHP code. The .htaccess file allows us to reconfigure Apache’s file handling rules at the directory level, telling it to treat other file extensions as PHP code as well.
Upload
.htaccessfile with content:AddType application/x-httpd-php .jpgThis reconfigures Apache in that directory to execute
.jpgfiles as PHP code (it could be any extension). TheAddTypedirective associates the MIME typeapplication/x-httpd-phpwith.jpgfiles, instructing Apache to pass them to the PHP interpreter.Upload
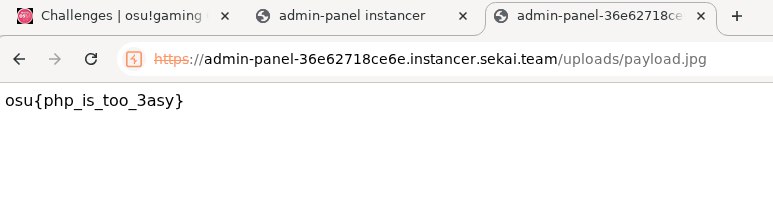
payload.jpgwith content:Access the file to execute the code and retrieve the flag.
The
<?=short tag is used here as an alias for<?phpto bypass any code filtering. According to PHP documentation, the<?=shorthand is always available.