TombWatcher writeup
TombWatcher is a Windows Active Directory box that involves lateral movement through multiple user accounts, Kerberoasting, shadow credential attacks, and certificate template abuse. We will perform BloodHound enumeration, set a service principal name for Alfred, Kerberoast to obtain Alfred’s hash, then leverage GenericAll permissions to manipulate SAM, John, and CERT_ADMIN accounts, finally using ESC1 vulnerability to request a certificate as the domain administrator.
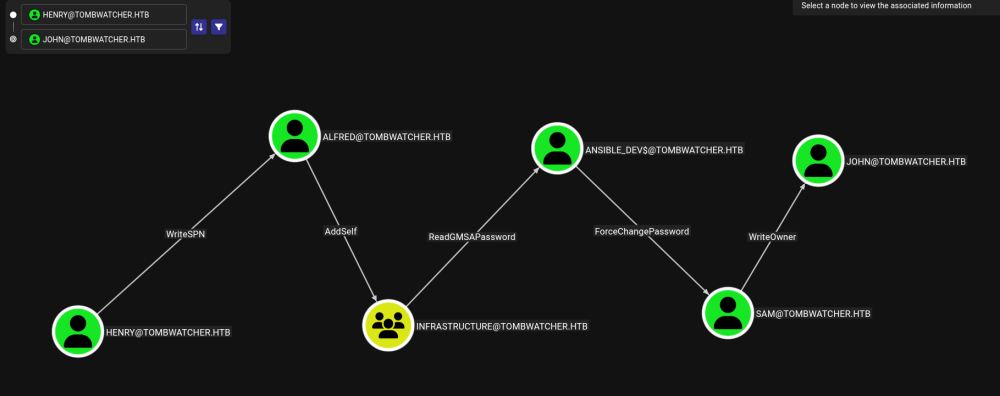
Exploitation path
HENRY
Start by collecting BloodHound data with rusthound:
Use bloodyAD to set a service principal name (SPN) for the ALFRED account:
Fix clock skew with the domain controller:
Perform Kerberoasting with netexec (nxc):
Crack the obtained hash with hashcat:
Remove the SPN from ALFRED (cleanup):
ALFRED
Add ALFRED to the infrastructure group:
Enumerate Group Managed Service Accounts (gMSA):
ANSIBLE_DEV$
Set a new password for the SAM account:
SAM
Set ownership of the JOHN account to SAM:
Grant GenericAll permission on JOHN to SAM:
Perform a shadow credential attack against JOHN using Certipy:
JOHN
Find certificate templates vulnerable to ESC1/ESC2:

Connect via Evil‑WinRM with John’s NTLM hash:
Inside the shell, locate a deleted object with a known SID:
Get-ADObject -Filter 'objectsid -eq "S-1-5-21-1392491010-1358638721-2126982587-1111"' -Properties * -IncludeDeleted
Restore the deleted object (CERT_ADMIN):
Restore-ADObject -Identity 938182c3-bf0b-410a-9aaa-45c8e1a02ebf
CERT_ADMIN
Perform another shadow credential attack against CERT_ADMIN:
Check for vulnerable certificate templates again:
Getting a sign certificate
Request a certificate with the “Certificate Request Agent” application policy:
Then request a certificate on behalf of the administrator:
Authenticate with the obtained administrator certificate:
Credentials
henry:H3nry_987TGV!
alfred:basketball
ansible_dev$:2669c6ff3a3d9c7472e358c7a792697b
sam:pass
john:ad9324754583e3e42b55aad4d3b8d2bf
cert_admin:f87ebf0febd9c4095c68a88928755773
administrator:f61db423bebe3328d33af26741afe5fc